Scenario Parameters
Introduction
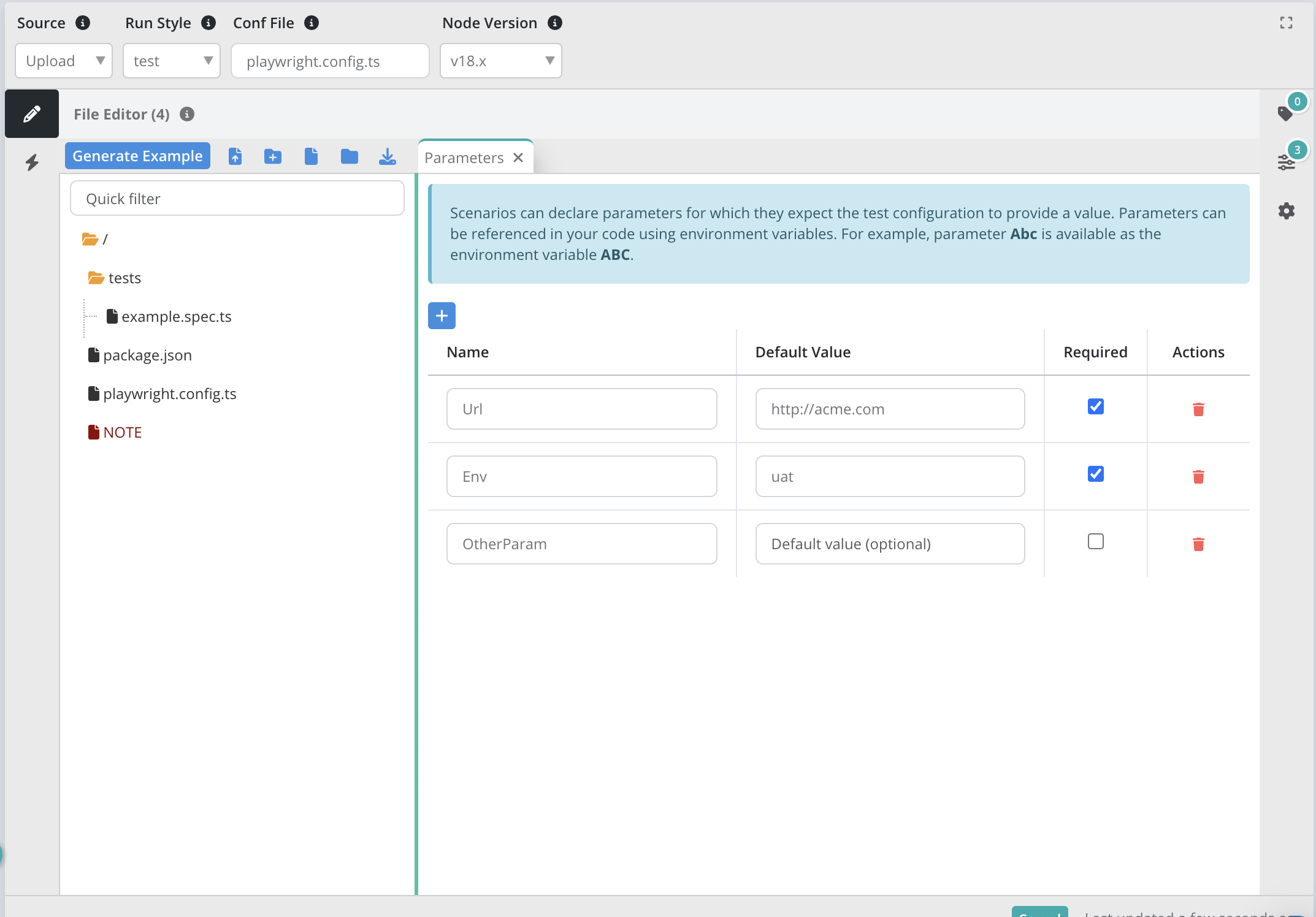
Scenario parameters allow you to pass parameters into your scenario from a test configuration. This enables sharing a single scenario definition across many different test configurations. Scenario parameters are often used to set the target URL of a test, credentials, number of virtual users, timeouts, etc.
Scenarios can declare parameter names in the Declared Params section. When you create a test configuration and choose that scenario, any declared parameters will automatically appear and prompt you for a value. The test configuration can also add additional parameters as required.
During test execution, scenario parameter values can be accessed as environment variables, system properties, or a params object depending on the scenario type chosen (i.e. Node.js script, JMeter, Gatling, Locust, Selenium, PhantomJs/SlimerJs, etc).
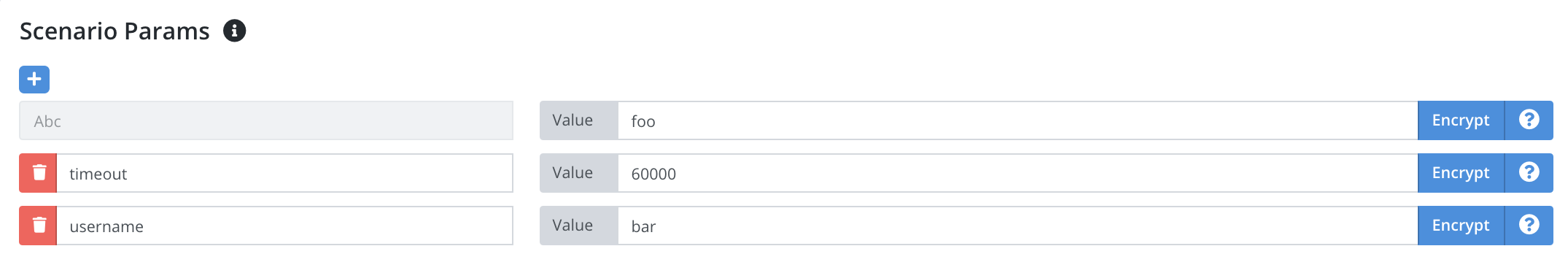
Scenario parameter values can be encrypted.
Declaring Parameters
Within any scenario there is a Parameters tab available by clicking the 2nd icon down on the right side. Declare any parameters here including whether or not they should be required or not. Any parameters declared here will appear when creating a test configuration and this scenario is chosen.
Setting Parameters
Each test configuration that uses a scenario will be able to set different values for declared parameters as well as adding additional parameters. Parameter values can be set via the website or via the API.
Setting Parameters via the Website
See the Scenario Params section of the test configuration setup screen.
Setting Parameters via the API
-
Trigger URL: Each test configuration has one or more trigger URLs. You can pass a parameter values as query parameters or in the body as a JSON object. See the trigger URL documentation for more details
-
Simple API: When triggering a test via our simple API you can pass parameters using the
params[*]parameter. So for example:-F "params[url]=https://google.com".
Accessing Parameters
In your scenario you can access the parameter value using a variety of approaches:
- As environment variable
[name]where name is the name of the parameter in upper case with any spaces removed. - As a system property with the same name as the parameter name. Only available for JMeter and Selenium Java scenarios.
- With the
paramsobject for Node.js, PhantomJS, and SlimerJS scripts. For example parameterAbcis accessible withparams['Abc'].
Encrypting Parameters
See our encryption guide for more details on how to encrypt parameters.