Encryption
- What Can Be Encrypted?
- How Does It Work?
- Download Public Key
- Encrypt Value Locally
- Bring Your Own Key
Testable Cloud’s philosophy is to encrypt all data and provide customer’s a way to further protect their data by bringing their own encryption key.
What Can Be Encrypted?
First level: Our databases are encrypted at rest using a Testable AWS KMS key.
Second level: The following are further encrypted using a public/private RSA key pair that is generated for each test case: scenario parameters, scripts, uploaded files, output files, and traces. Users can download the public key and pre-encrypt data before uploading it to Testable as well.
Third level (enterprise customers only): Bring your own encryption key by granting us access to the key via either the AWS, Azure, or Google Cloud key management service. This key will then be used to encrypt each test case’s private key.
How Does It Work?
Each test case has a unique 2048 bit public/private RSA key pair.
Data is encrypted using a uniquely generated 256-bit AES symmetric key and IV. The symmetric AES key is encrypted into the data using the RSA public key and included with the encrypted data contents.
Each test case’s public key is available for download so that data can also be encrypted locally.
Data is decrypted at the last possible moment, either just before sending to the test runners for execution over an SSL connection or as a response to an API request over an SSL connection. Decrypted data is not stored or logged anywhere by Testable.
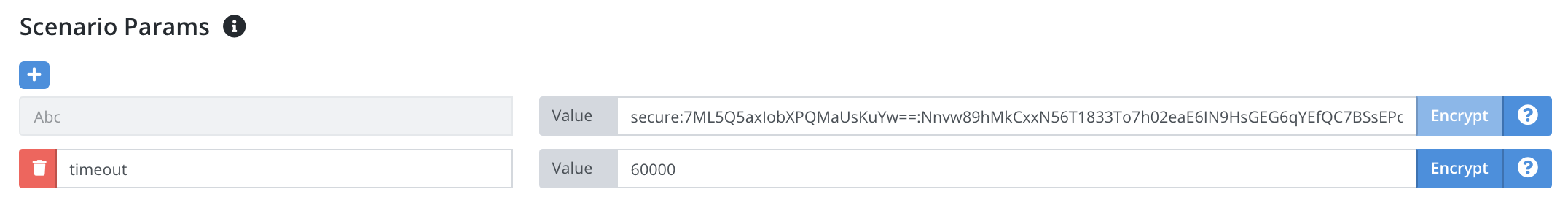
Encrypted data has the format secret:[IV]:[rsa-encrypted-aes-key]:[aes-encrypted-contents].
For scenario parameters you can encrypt any parameter value easily via our website. Next to any parameter there is an Encrypt button that will encrypt the value using that test case’s public key.
For other data like scripts, uploaded files, output files, and traces encryption happens automatically.
Download Public Key
There are 2 ways to download your public key.
-
https://api.testable.io/test-cases/[testCaseId]/key. The
testCaseIdis the number after https://a.testable.io in the URL when viewing a test case on our website. -
Click on any test case and in the upper right click the certificate icon.
Encrypt Value Locally
Use openssl to encrypt a value locally once you’ve downloaded the test case’s public key. Here is an example script that assumes your test case public key is saved at testable-key-123.pub:
#!/bin/bash
# contents to encode
contents="my secret text"
# generate a random key (32 byte) and iv (16 byte)
key=$(openssl rand -hex 32)
iv=$(openssl rand -hex 16)
# encrypt the key using the RSA public key for the test case
encryptedAesKey=$(echo -n "$key" | xxd -r -p | openssl rsautl -encrypt -pubin -inkey testable-key-123.pub -out >(base64))
# encrypt the contents using your key + iv
encryptedContents=$(echo -n $contents | openssl enc -aes-256-cbc -K $key -iv $iv -base64)
# convert your hexadecimal iv to base64 as required by Testable
ivb64=$(echo -n $iv | xxd -r -p | base64)
# format to store as your parameter value on Testable
echo "secure:$ivb64:$encryptedAesKey:$encryptedContents"
The final output can be used as a scenario parameter or uploaded to Testable.
Bring Your Own Key (Enterprise Only)
Private keys for each test case are stored encrypted using an AWS KMS key in Testable’s account by default. You can also choose to have Testable encrypt using your own AWS KMS key, Azure Key Vault key , or GCP Key Ring key. To do this you need to setup your cloud account as a test runner source first (Org Management => Test Runner Sources) and then choose your account for the Encryption field at Org Management => Settings. This feature is for Enterprise plans only.